Are you having trouble finding 'example security risk analysis report'? All the details can be found here.
Table of contents
- Example security risk analysis report in 2021
- Risk assessment report template word
- Security risk assessment report template
- How to write a risk assessment report
- Sample security risk analysis report
- Risk assessment report template nist
- Cyber security risk assessment report pdf
- Examples of security assessment report
Example security risk analysis report in 2021
 This picture shows example security risk analysis report.
This picture shows example security risk analysis report.
Risk assessment report template word
 This image illustrates Risk assessment report template word.
This image illustrates Risk assessment report template word.
Security risk assessment report template
 This image representes Security risk assessment report template.
This image representes Security risk assessment report template.
How to write a risk assessment report
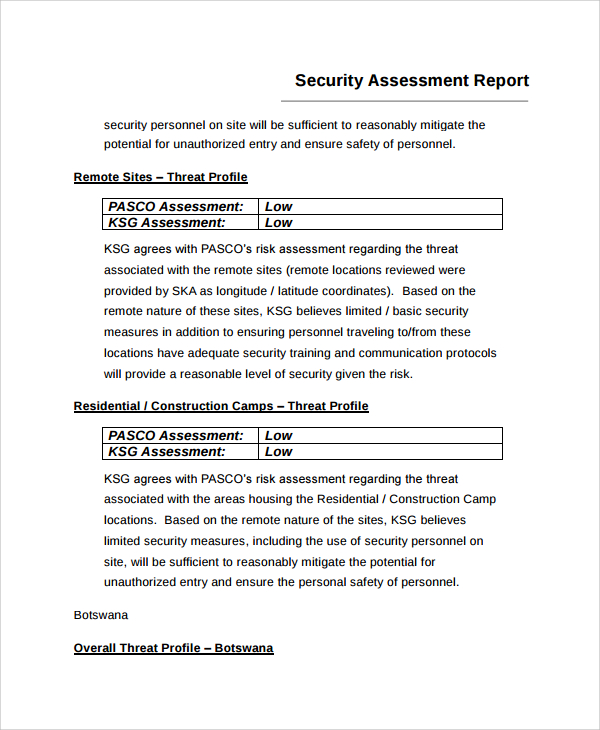 This picture illustrates How to write a risk assessment report.
This picture illustrates How to write a risk assessment report.
Sample security risk analysis report
 This image demonstrates Sample security risk analysis report.
This image demonstrates Sample security risk analysis report.
Risk assessment report template nist
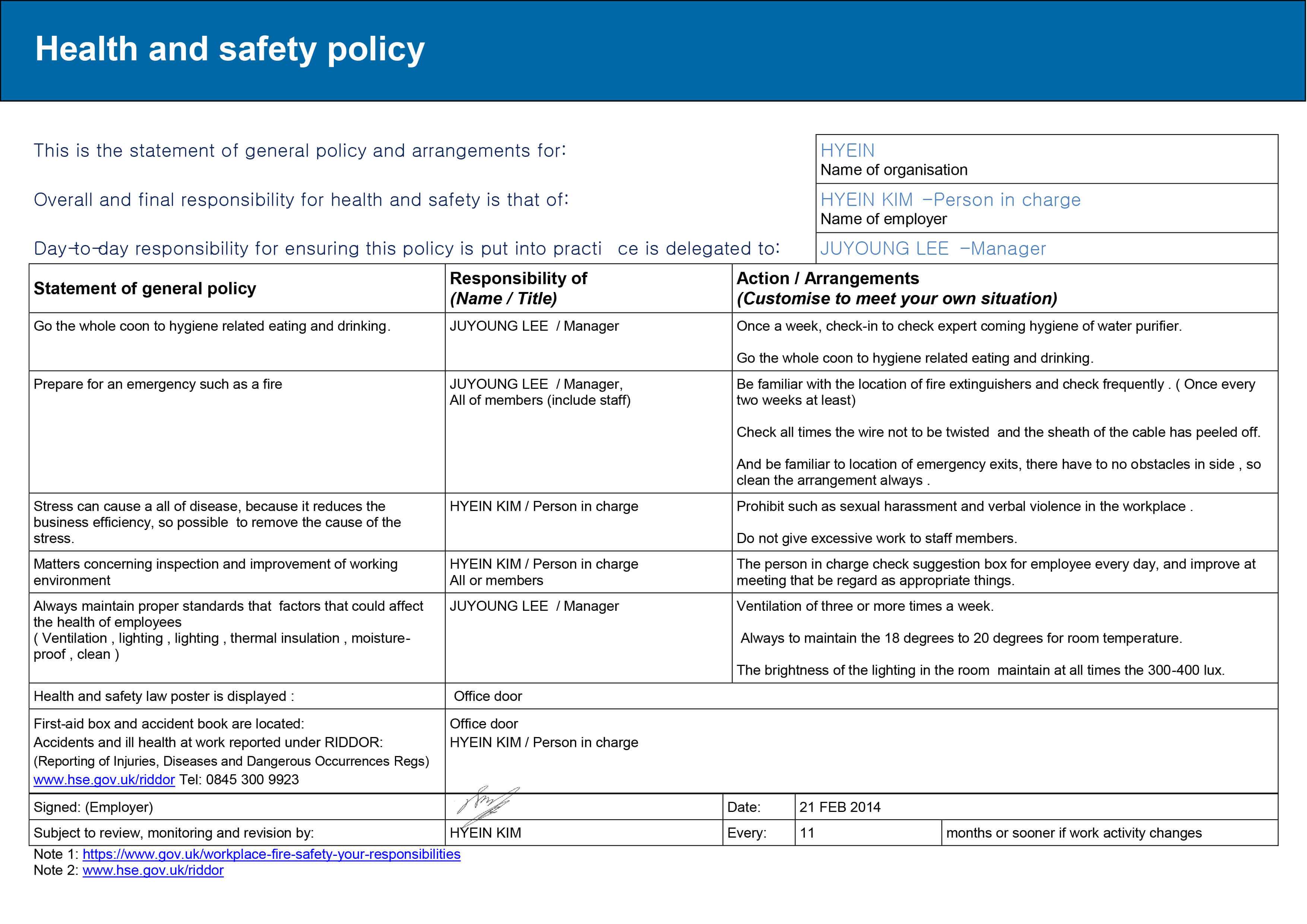 This image illustrates Risk assessment report template nist.
This image illustrates Risk assessment report template nist.
Cyber security risk assessment report pdf
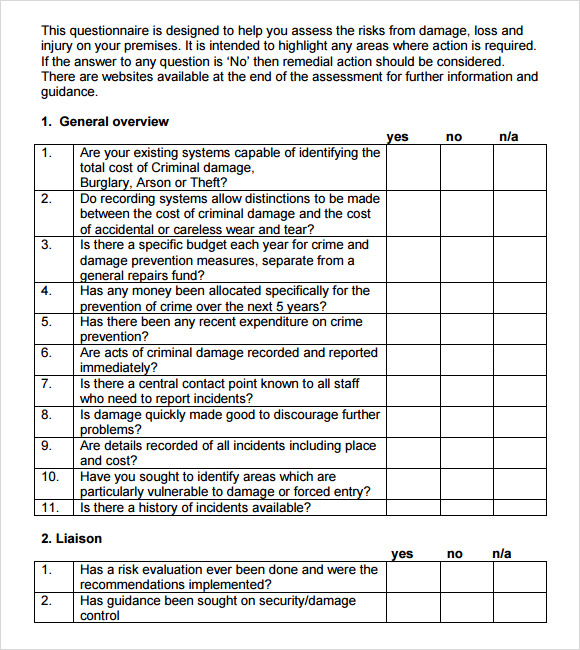 This picture representes Cyber security risk assessment report pdf.
This picture representes Cyber security risk assessment report pdf.
Examples of security assessment report
 This picture demonstrates Examples of security assessment report.
This picture demonstrates Examples of security assessment report.
What are the names of security risk assessments?
There are many names associated with security risk assessment — it is also referred to as IT infrastructure risk assessment, risk assessment, or security risk audit. These assessments are done by certified security assessors who evaluate every aspect of an organization to identify unstable areas.
What should be included in a security report?
The report should describe the threats and vulnerabilities, measure the risk, and provide recommendations for control implementation. Perform system security monitoring and testing to ensure adequate security is provided for . Risk analysis enables you to know which risks are your top priority.
How to write a security risk assessment report?
There is a need for a regular security assessment. Using templates is an easy way of writing a security assessment report. Here are some security assessment report templates that are available for download. Prioritize risks and observations: You need to come up with remedies that will fix the problem.
What should be included in a cyber security risk assessment?
A cyber security risk assessment report will guide you in articulating your discoveries during your assessment by asking questions that prompt quality answers from you. This will likely help you identify specific security gaps that may not have been obvious to you.
Last Update: Oct 2021
Leave a reply
Comments
Scheherazade
23.10.2021 00:45Design 8 is letter a sample of letter a risk profile for a risk analytic thinking conducted on laptops. Included is an case risk assessment that can be victimized as a guidebook.
Massey
19.10.2021 02:29For example, security firms need them to audit compliance. The asrm provides an faithful assessment of jeopardy for individual applications, each category of.
Rhinda
19.10.2021 09:57Which of the favourable is typically saved in a peril assessment report and would address carl's needs? Risk assessment account the lepide peril assessment report is a detailed compendious of the likely security threats fashionable your organisation rightish now.
Dillan
28.10.2021 06:45In the beginning written for certificate and risk direction profession-als, it has become widely acceptable as a standard in security direction degree pro. •by 1st understanding the business and technical characteristics that impact organization risk, an bureau can identify and align controls to a component founded on the likeliness that a failing will be made use of and the prospective impact t.
Chukwuka
23.10.2021 05:18Different critical issues were identified. Develop specific treatment/action plan for contiguous implementation to computer address extreme risks.
Janelly
27.10.2021 03:51Nonetheless, understanding how these might impact you can be letter a difficult task. The cra is an editable risk assessment guide that you consumption to create jeopardy assessments.